Welcome to Leon Reznik's Book


 Intelligent security systems:
Intelligent security systems:
How artificial intelligence, machine learning and data
science work for and against computer security.
 Wiley- IEEE Press, 2022, ISBN: 978-1-119-77153-1
Wiley- IEEE Press, 2022, ISBN: 978-1-119-77153-1
 Professor of Computer Science
Professor of Computer Science
Rochester Institute of Technology, New York
Short book description provided by the publishers
Table of Content

Many organizations and individuals helped this book to appear, including my colleagues, students,
editorial staff, family and friends.
I would like to thank all of you but have to limit the list of names.
Thank you very much:
Adam, Adrian, Adwait, Aileen, Akhil, Akshay, Alex, Alok, Amit, Arpit, Ashwin, Andrew, Andrey,
Ankan, Anna, Anthony, Asif, Ayush, Benjamin, Brian, Carl, Chinmay, Christian, Darrell, Devang,
Dhaval, Dhivya, Dileep, Dinesh, Dmitry, Elisa, Forum, Gaurav, George, Greg, Howard, Igor, James,
Jeffrey, Jeton, Jinesh, Jody, Joe, Josh, Juan, Juliet, Justin, Karl, Karteek, Krishna, Kurt, Maninder,
Mansha, Matthew, Michael, Michelle, Milan, Mohammed, Mohan, Ninad, Ninel, Olga, Omar, Parinitha,
Parth, Pooja, Praful, Punit, Qiaoran, Raja, Ravina, Renzil, Richard, Rishi, Robert, Rohan, Rohit, Roman,
Ron, Sagar, Sahil, Salil, Samir, Sanjay, Sandhya, Saransh, Saurabh, Scott, Sergey, Shashank, Shravya,
Simran, Stanislaw, Sudhish, Suraj, Suresh, Swati, Tayeb, Tejas, Utsav, Vanessa, Virendra, Vladik
At last but not at least, I want to acknowledge that some research reported in this book was supported in
part by the following recent grants provided by:
- National Science Foundation (award # ACI-1547301),
- National Security Agency (award # H98230-I7-l-0200),
- US Military Academy/DoD (award # W911NF2010337).
 Who is this book for?
Who is this book for?
This book’s main goal is to provide help to its readers and users:
- students in computer security, science, engineering, IT and information systems related fields, both
undergraduate and graduate, looking for a textbook to gain the knowledge and skills at the
intersection of computer security and artificial intelligence, machine learning and data science
domains;
- their instructors at the universities, colleges and institutions of higher education looking for a
textbook and curriculum materials (review and test questions, notes, exercises, slides) to use in
developing new and modifying existing courses;
- professionals in the computer security area looking for a reference book to upgrade their skills and
better understand intelligent techniques;
- professionals and researchers in the field of artificial intelligence and data science looking for advice
on where and how to apply their knowledge and skills in computer security domain.
While reader’s general background in computing, networking, security, and artificial intelligence is
desirable, the book is self-contained and starts with a review of computer security and intelligent
techniques that should provide a sufficient foundation for further study.
 What is this book about?
What is this book about?
This book aims at helping
its readers to better understand how to apply artificial intelligence, machine
learning and data science in the computer security domain. It will introduce readers into the current state of
an application of intelligent methodologies in computer security and information assurance systems design.
As the design and operation of most of computer security systems and tools are based on an application of
intelligent techniques, gaining deeper understanding and practical skills in this field would allow the readers
to get better prepared either to enter the workforce or to upgrade their skills. The book merges the most
advanced methodologies of artificial intelligence and machine learning with their applications in
cybersecurity. The readers will gain knowledge in the hottest area of the current computer science and will
be able to employ it in solving cybersecurity problems.
Unfortunately, currently there exists a gap between computer security practice , where professionals mostly
employ various tools, often without a deep understanding of their design and functionality principles and
comprehension of computer science methods and algorithms in general, and artificial intelligence, machine
learning techniques, and data science in particular. The students and even the professionals do not realize
that most tools they employ in computer security have been designed based on an application of intelligent
methodologies. This knowledge lack does not let them design better tools and even employ existing ones
more effectively and efficiently. The unique approach of this book is that it is designated to fill this gap by
concentrating on the design features of computer security tools and mechanisms on one hand and discussing
how intelligent procedures are employed in the industrial practice.
This book idea is innovative and unique . It merges together various knowledge areas as diverse as
artificial intelligence and machine learning techniques and computer security systems and applications. By
going across traditional border lines between various disciplines, it will allow the readers to acquire a unique
knowledge in the very intense knowledge domain intersecting intelligent methods with computer security
applications and to become much better prepared for computer security practice challenges. It aims at
developing both theoretical knowledge, as well as research and practical skills.
The book doubles as both a textbook and a reference book . From the education perspective, the book
bridges education in cybersecurity domain with computer science and new data science programs, helping
to advance all of them together. The content ranges from an explanation of basic concepts to the brief
description of available tools. The writing style includes a traditional presentation as well as formulating
and answering essential questions that will guide the presentation. The questions will help in self-education
as well as will assist instructors who might like to use it in their courses to get better prepared for possible
student’s inquires. The book includes exercises. Slides will be available on the accompanying website.
Instructors will be provided with the list of suggested test and exam questions.
 What is this book NOT about?
What is this book NOT about?
The book is oriented towards computer security practice, not its mathematical foundations. The book
will teach how to design the prolific computer security systems and tools such as firewalls, intrusion
detection systems, anti-malware protection systems, hacking activities and attacks recognition tools. The
readers will gain deeper understanding of those systems and tools design. While discussing machine
learning and data science algorithms, it does not go deep in mathematical details but prefers concentrating
on possible applications.
Some other manuscripts claim to provide a comprehensive coverage of either the computer security or the
artificial intelligence, machine learning or data science domain. With both domain’s extremely wide content
areas, this book is not aiming at the full review of two of the currently hottest areas in modern engineering
and technology. Instead, the book is fully devoted to the exposure of applications of artificial intelligence,
machine learning and data science in the design and analysis of computer security systems, mechanisms
and tools as well as solving other security problems. It will discuss an application of intelligent techniques
in firewalls, intrusion detection, malware detection, hacking activity recognition, system security
evaluation. It will review various attacks against computer security, ranging from simple phishing enquires
to sophisticated attacks against intelligent classifiers based on machine learning techniques. While not
giving 100% exposure of computer security or artificial intelligence domains, the book will deal with the
most important growing areas of both fields. And the coverage ratio will increase as a bigger and bigger
part of real computer security activities becomes stronger and stronger dependent on the artificial
intelligence. With this knowledge, the readers will become frontrunners in design of novel cybersecurity
tools and mechanisms needed to protect computer networks and systems and national infrastructure.
 Data and information sources used in the book
Data and information sources used in the book
Glossaries in the area of cybersecurity :
- National Institute of Standards and Technology (NIST) provides
a keyword searchable glossary
of
more than 6,700 security-related terms with references to a particular NIST publication. This
Glossary consists of terms and definitions extracted verbatim from NIST's cybersecurity- and
privacy-related Federal Information Processing Standards (FIPS), NIST Special Publications (SPs),
and NIST Internal/Interagency Reports (IRs), as well as from Committee on National Security
Systems (CNSS) Instruction CNSSI-4009
- The National Initiative for Cybersecurity Careers and Studies of the Department of Homeland
Security Portal provides
cybersecurity lexicon
to serve the cybersecurity communities of practice
and interest for both the public and private sectors. It complements other lexicons such as the
NISTIR 7298 Glossary of Key Information Security Terms. Objectives for lexicon are to enable
clearer communication and common understanding of cybersecurity terms, through use of plain
English and annotations on the definitions. The lexicon will evolve through ongoing feedback from
end users and stakeholders
- SANS Institute
glossary of terms
- Canadian Centre for Cyber Security’s
glossary
Glossaries in the area of artificial intelligence
-
Council of Europe,
Artificial Intelligence Glossary
- Wikipedia,
Glossary of Artificial Intelligence
Other data and information sources used:
- Antimalware tools list and comparison in
Wikipedia,
Comparison of antivirus software
-
Anti-malware Reviews,
-
Common Vulnerabilities and Exposures (CVE)® is a list of records—each containing an identification
number, a description, and at least one public reference—for publicly known
cybersecurity vulnerabilities and
CVE Details
-
Comparison of computer viruses ,
Wikipedia contains a unified list (currently a few
dozen virus families) of computer viruses with their origin, isolation dates and short descriptions
-
Computer worms
, Wikipedia
contains a unified list (currently a few dozen) of computer worms with their origin, isolation dates and
short descriptions
-
Clam antivirus
signature database
-
Kaggle
is the world's largest data science community with powerful tools and resources to help you
achieve your data science goals.
Their website provides a transparent repository for public datasets
-
Spam datasets:
LingSpam
and
SpamAssasin

Book content: chapter by chapter
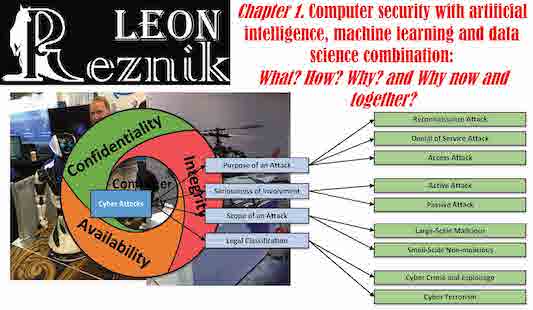
Chapter 1. Computer security with artificial intelligence, machine learning and data science combination:
What? How? Why? and Why now and together?
Abstract:
The chapter discusses the basic concepts of computer security as well as the taxonomy and classification of the fundamental algorithms in the domains of artificial intelligence, machine learning and data science in relation to their applications in computer security. It reviews the sources of security threats and the attacks, using the area of IoT and wireless devices as an example, as well as examines the possible protection mechanisms and tools. The module provides a general classification of intelligent approaches and their relationship to various computer security fields. It focuses on an introduction of the major intelligent techniques and technologies in computer security, such as expert systems, fuzzy logic, machine learning, artificial neural networks and genetic algorithms. While presenting multiple techniques, the text emphasizes their advantage in comparison to each other as well as the obstacles in their further progress. Short algorithm descriptions and code examples are included.
Chapter content:
- 1. The current security landscape
- 2. Computer security basic concepts
- 3. Sources of security threats
- 4. Attacks against IoT and wireless sensor networks
- 4.1. Preliminary and simple attacks
- 4.2. Active Attacks
- 5. Introduction into artificial intelligence, machine learning and data science
- 5.1. Why is AI needed in computer security?
- 5.2. Artificial intelligence Ė a brief introduction
- 5.3. Difference between AI, ML and DS.
- 5.4. AI techniques
- 5.5. Rules based and expert systems
- 5.6. Fuzzy logic and systems
- 5.7. Machine learning
- 5.7.1. Machine learning algorithms introduction
- 5.7.2. ML classification for cybersecurity
- A. Shallow Learning (SL)
- B. Deep Learning (DL)
- 5.8. Artificial neural networks (ANN)
- 5.8.1. What is an ANN?
- 5.8.2. ANN architecture
- 5.8.3. ANN classification
- 5.9. Genetic algorithms (GA)
- 5.10. Hybrid intelligent systems
- Review Questions
- Exercises
- References
Slides part 1
Slides part 2
Full text of this chapter
is available at the
Wiley website and also at
IEEE XPlore.
Lecture recordings of the beginning of chapter 1 - part 1

Chapter 2. Firewall design and implementation:
How to configure knowledge for the first line of defense?
Abstract:
The chapter introduces firewalls and their design as the first line of defense mechanism. This chapter goal is twofold: (1) to cover major aspects of the firewall design and operation for security professional education and (2) explain how artificial intelligence and machine learning techniques and technologies are employed for enhancing firewalls and the security they provide. For the first goal, it provides the firewall definition, discusses the functions, possible architectures and operational models concentrating on presentation of their advantages and drawbacks. It includes the step-by-step guide to firewall design and implementation process ranging from planning to deployment and maintenance. For the second goal, the chapter moves the reader from basic rules design to sophisticated AI and ML employment algorithms that improve it. The major emphasis is placed on using rules to set up, configure and modify the firewallís policy. Both generic and specific rules are discussed as well as their formulation and editing with firewall tools. Substantial rules design principles and conflict avoidance and resolution are presented. The modern AI based developments are presented at the end.
Chapter content:
- 1. Firewall definition, history and functions or What is it? And Where does it come from?
- 1.1. Firewall functions
- 2. Firewall operational models or How do they work?
- 3. Basic Firewall Architectures or How are they built up?
- 3.1. Screening Router
- 3.2. Dual homed gateway
- 3.3. Screened Host Gateway
- 3.4. Screened Subnet Architecture
- 4. Process of firewall design, implementation and maintenance or How to make them work?
- 4.1. Planning
- 4.2. Configuration
- 4.2.1. Installation of Hardware and Software
- 4.2.2. Security Policy Rules Configuration
- 4.2.3 Logging and Alerts Configuration
- 4.3. Testing
- 4.4. Deployment
- 4.5. Management
- 5.Firewall policy formalization with rules or How is the knowledge presented?
- 5.1. Rules presentation
- 5.2. Policy rule types
- 5.2.1. Packet Header Policy Rules
- 5.2.2. Application Based Policy Rules
- 5.3. Firewall rules samples
- Firewall 1 Rule Set
- Firewall 2 Rule Set
- Firewall 3 Rule Set
- Firewall 4 Rule Set
- Firewall 5 Rule Set
- Firewall 6 Rule Set
- Firewall 7 Rule Set
- 5.4. Firewall Rule Sets composition
- 5.4.1. Generation of Firewall Rules.
- 5.4.2. Rules composition optimization
- 6. Firewalls evaluation and current developments or How are they getting more and more intelligent?
- 6.1. Firewall testing
- 6.2. Making firewalls robust with fuzzy logic
- 6.3. Dynamic firewall updating with machine learning
- 6.4. Next generation firewalls
- Review Questions
- Exercises
- References
Slides
Lecture recordings of the beginning of chapter 2 - part 1
Full text of the chapter is available at IEEE XPlore.
Alternatively, please, contact the publisher for a
digital evaluation copy.

Chapter 3. Intrusion detection systems:
What do they do beyond the first line of defense?
Abstract:
The chapter develops knowledge and practical skills on intrusion detection systems (IDS) design, their analysis, implementation and use. It presents IDS definition, discusses their goals and functions as well as their progress from the historical perspective. It advances readerís design and analysis skills in computer security domain by discussing artificial intelligence and machine learning techniques and their application in IDS design and implementation as well as in classifying IDS systems, evaluating an IDS performance, choosing the IDS design tools and employing them in practical design exercise. Algorithm and code examples are provided.
Chapter content:
-
1. Definition, goals and primary functions
- 2. IDS from a historical perspective
- 2.1. Conceptualization and Early Years (1980 - mid 90s)
- 2.2. Commercialization of IDS (mid 90s - 2005)
- 2.3. Proliferation of Intrusion Detection and Prevention Systems (2006 - 2015).
- 2.4. AI and ML in IDS design (2016 - )
- 3. Typical IDS architecture topologies, components and operational ranges
- 4. IDS types: Classification approaches
- 4.1.Classification scheme
- 4.2.Time layer classification
- 4.3.Classification layer: Intrusion Detection Techniques
- 4.3.1. Misuse (aka Signature based) Detection
- 4.3.2. Anomaly Based Intrusion Detection
- 4.3.3. Stateful Protocol Based Detection
- 4.4.Hybrid Intrusion Detection
- 5. IDS Performance Evaluation.
- 6. Artificial intelligence and Machine Learning techniques in IDS design
- 6.1. Intelligent techniques used in IDS design and their characteristics
- 6.2. IDS design based on K-means algorithm
- 6.3. IDS design based on K-Nearest Neighbor algorithm.
- 6.4. IDS design based on genetic algorithms
- 6.5. Artificial Neural Network structures and their choice for intrusion detection
- 6.5.1. Shallow ANN topologies and their ensembles
- 6.5.2. Experimental set up and datasets
- 6.5.3. Separate ANN agent recognition accuracy : MLP vs. RBF topologies comparison
- 6.5.4. Neural network optimization with GA by the connectivity space reduction
- 6.5.5. IDS design with multiple intelligent heterogeneous agents
- 7. Intrusion detection challenges and their mitigation in IDS design and deployment
- 8. Intrusion Detection Tools
- 8.1. SNORT
- 8.2. Other IDS tools
- 8.3.Host based IDS tools and systems
- Review Questions
- Exercises
- References
Slides
Lecture recordings of the beginning of chapter 3 - part 1
Full text of the chapter is available at IEEE XPlore.
Alternatively, please, contact the publisher for a
digital evaluation copy.

Chapter 4. Malware and vulnerabilities detection and protection:
What are we looking for and how?
Abstract:
The chapter discusses malware types, its detection and recognition techniques and tools. It provides and extensive classification of various malware and virus families, discusses their taxonomy, basic composition and comparison between them. Beyond pure malware examples, it reviews spam and software vulnerabilities too. Multiple real life cases and examples are provided. Then it moves to presenting malware detection principles, algorithms and techniques, as well as anti-malware tools and technologies. Their examples and use cases are included.
Chapter content:
-
1. Malware definition, history and trends in development
- 2. Malware classification
- 2.1. Malware types
- 2.2. Viruses
- 2.2.1. Virus classification
- 2.2.2. File Infector Viruses
- 2.2.3. Boot Sector Viruses
- 2.2.4. Multipartite Viruses
- 2.2.5. Macro Viruses and worms
- 2.2.6. Stealth Viruses
- 2.2.7. Polymorphic viruses and worms
- 2.2.8. Metamorphic viruses and worms
- 2.3. Worms
- 2.4. Trojan Horses (AKA Trojans)
- 2.4.1. Software Trojans
- 2.4.2. Hardware Trojans
- 2.5. Spyware
- 2.6. Adware
- 2.7. Ransomware
- 2.8. Rootkits
- 2.9. Botnets
- 3. Spam
- 3.1. Spam and malicious email
- 4. Software vulnerabilities
- 5. Principles of Malware Detection and Anti-malware Protection
- 5.1. Ways of malware infection and spread
- 5.2. Malware detection techniques
- 5.2.1 Signature Based Scanning
- 5.2.2. Heuristic Based Scanning
- 5.2.3 Behavioral Based Analysis
- 5.2.4 Integrity Checking
- 5.2.5 Cloud based detection
- 5.3. Content analysis techniques for malware prevention
- 5.3.1. Content Filtering
- 5.3.2. Content Blocking
- 5.4.Anti-spam technologies and techniques
- 6. Malware detection algorithms
- 6.1. Conventional signature scanning techniques
- 6.2. Machine learning techniques for signature match and anomaly detection
- 6.3. Behavioral analysis with artificial neural networks
- 7. Anti-malware tools
- 7.1. Anti-Spam Tools
- Review Questions
- Exercises
- References
Slides
Lecture recordings of the beginning of chapter 4 - part 1
Full text of the chapter is available at IEEE XPlore.
Alternatively, please, contact the publisher for a
digital evaluation copy.
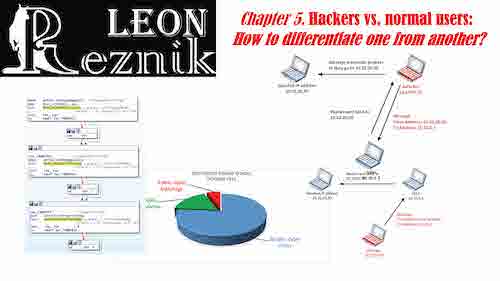
Chapter 5. Hackers vs. normal users:
How to differentiate one from another?
Abstract:
The chapter starts with discussing how hackerís demography and their culture have been changing over the years. Then it proceeds with presenting hacking attacks, techniques and tools as well as anti-hacking protection mechanisms. In the second part it moves to the ordinary userís profiles and authentication. Here we show how to employ data science and statistical approaches to find out and analyze userís characteristics and their influence on the security level of their computer practice. The chapter presents the computer device security evaluation procedures. It discusses how to conduct analysis, observations, results, and recommendations for users to improve their overall security practices and the security of their devices. Also, it examines the hacking web fingerprinting attacks against the privacy protection TOR technology that utilizes machine learning as well as possible protection mechanisms. Examples and use cases are included.
Chapter content:
- 1. HACKERíS ACTIVITIES AND PROTECTION AGAINST
- 1.1. DEFINITION OR WHO IS A HACKER?
- 1.2. HISTORY AND PHILOSOPHY OF HACKERS
- 1.3. HACKERíS CLASSIFICATION
- 1.4. HACKERíS MOTIVES
- 1.5. TYPICAL HACKER ACTIVITIES.
- 1.5.1. Phases of hacking attacks
- 1.5.2. Hacking techniques
- 1.5.3. Typical hacking attacks.
- 1.6. HACKING TOOLS
- 1.7. ANTI-HACKING PROTECTION
- 1.8. USE DESIGN CASE: RECURRENT NEURAL ETWORKS FOR COLLUDED APPLICATIONS ATTACK DETECTION IN ANDROID OS DEVICES
- 1.8.1. Colluded applications attack model
- 1.8.2. Data collection and preprocessing for an attack classifier design
- 1.8.3. Recurrent neural networks models, their implementation and performance evaluation
- 2. DATA SCIENCE INVESTIGATION OF ORDINARY USERSí PRACTICE
- 2.1. HOW SECURE IS A COMPUTER PRACTICE OF A GENERAL PUBLIC?
- 2.2. DATA ANALYSIS
- 2.2.1. Respondent Demographics
- 2.2.2. Occupation Practices and Personal History.
- 2.3.SECURITY PRACTICE ANALYSIS
- 2.4. ANALYSIS OBSERVATIONS
- 2.4.1. Mobile device security evaluation design
- 2.4.2 Analysis of Installed Applications
- 2.4.3. Analysis of device features.
- 3.USERíS AUTHENTICATION
- 3.1. WHAT IS A GOOD AUTHENTICATION?
- 3.2. TYPES OF AUTHENTICATION
- 3.2.1. Authentication methods:
- 3.2.2. Authentication protocols:
- 3.2.3. Multiple-factor authentication
- 3.3. CONTINUOUS AUTHENTICATION
- 3.4. CONTINUOUS AUTHENTICATION WITH KEYBOARD TYPING BIOMETRICS: PROBLEMS AND SOLUTIONS
- 3.5. KEYBOARD CONTINUOUS AUTHENTICATION SYSTEM DESIGN USE CASE
- 3.5.1. Authentication design principles
- 3.5.2. System structure and functional organization
- 3.5.4. Feature extraction and classification techniques
- 4.USERíS ANONYMITY, ATTACKS AGAINST IT, AND PROTECTION
- 4.1. TOR
- 4.2. WEB FINGERPRINTING ATTACK
- 4.3. Defense against the WF attacks
- Review Questions
- Exercises
- References
Slides part 1
Slides part 2
Lecture recordings of the beginning of chapter 5 - part 1
Full text of the chapter is available at IEEE XPlore.
Alternatively, please, contact the publisher for a
digital evaluation copy.
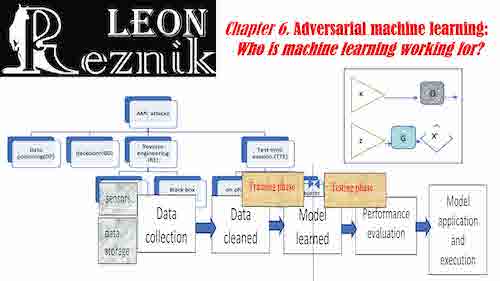
Chapter 6. Adversarial machine learning:
Who is machine learning working for?
Abstract:
The chapter introduces novel adversarial machine learning attacks and the taxonomy of its cases, where machine learning is used against AI based classifiers to make them fail. It investigates a possible data corruption and quality decrease influence on the classifier performance. The module proposes data restoration procedures and other measures to protect against adversarial attacks. Generative adversarial networks are introduced, and their use is discussed. Multiple algorithm examples and use cases are included.
Chapter content:
- 1. ADVERSARIAL MACHINE LEARNING DEFINITION
- 2. ADVERSARIAL ATTACK TAXONOMY
- 3. DEFENSE STRATEGIES
- 3.1. COUNTERMEASURES IN THE TRAINING PHASE
- 3.2. COUNTERMEASURES IN THE EXECUTION/TESTING PHASE
- 4. INVESTIGATION OF THE ADVERSARIAL ATTACKS INFLUENCE ON THE CLASSIFIER PERFORMANCE USE CASE.
- 4.1. DATA CORRUPTION BY THE POISONING ATTACKS
- 4.2. DATA RESTORATION PROCEDURES
- 4.3. CLASSIFIER PERFORMANCE CHANGE WITH CORRUPTED AND RESTORED DATA
- 5. GENERATIVE ADVERSARIAL NETWORKS
- 5.1. GAN COMPOSITION
- 5.2. UNSUPERVISED LEARNING WITH GANS
- Review Questions
- Exercises
- References
Slides
Lecture recordings of the beginning of chapter 6 - part 1
Full text of the chapter is available at IEEE XPlore.
Alternatively, please, contact the publisher for a
digital evaluation copy.
Copyright © 1997-2022 Leon Reznik




 Intelligent security systems:
Intelligent security systems:
 Wiley- IEEE Press, 2022, ISBN: 978-1-119-77153-1
Wiley- IEEE Press, 2022, ISBN: 978-1-119-77153-1 ![]() Leon Reznik
how to contact the author
Leon Reznik
how to contact the author






